
Why Choose AllConnected?
Learn what sets AllConnected apart from other MSPs and how we can help your business thrive in the digital age.

Learn what sets AllConnected apart from other MSPs and how we can help your business thrive in the digital age.

Learn the risks faced by businesses in today’s digital landscape and why it’s crucial to take proactive measures to address these challenges.

Learn why MFA is essential to any business, the key benefits Cisco DUO can provide, and how Cisco DUO can support compliance requirements.

In this blog post, we will explore how IT is transforming the financial industry and explore key ways technology can support the future of finance.

Learn more about AllConnected’s upcoming cybersecurity webinar and why cyber security is so important in today’s high threat landscape.
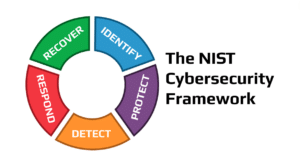
Learn more about the five pillars of the NIST framework and how they can be used to enhance cybersecurity within your organization.

Learn more about our recent webinar, panelists, the topics we covered, and why a strong, multi-layered cybersecurity defense is so important today.
Learn several key ways technology can support your business and drive revenue growth.

As you continue to review your cybersecurity strategy, we have put together a few of the most important cybersecurity questions to ask.

Ensure your devices stay protected and your data stays safe over the holiday season with our top tech tips.
AllConnected is a Premier Cisco-certified MSP, Veeam Gold Cloud Services Provider, and Microsoft partner providing tailored enterprise-class cybersecurity, scalable cloud infrastructure, and backup & recovery solutions based on the NIST 800-171 framework.
Whether your organization needs a fully outsourced IT team or co-managed support for existing resources, small-to-midsize businesses rely on AllConnected for a variety of advanced IT solutions, including:
Allconnected provides managed IT services To Los Angeles and Ventura County, including the following local communities:
Los Angeles County
Acton
Agoura Hills
Alhambra
Altadena
Arcadia
Artesia
Avalon
Azusa
Baldwin Park
Bell
Bell Gardens
Bellflower
Beverly Hills
Calabasas
Canyon Country
Carson
Castaic
Cerritos
City Of Industry
Claremont
Compton
Covina
Culver City
Diamond Bar
Dodgertown
Downey
Duarte
El Monte
El Segundo
Gardena
Glendora
Hacienda Heights
Harbor City
Hawaiian Gardens
Hawthorne
Hermosa Beach
Huntington Park
Inglewood
La Canada Flintridge
La Crescenta
La Mirada
La Puente
La Verne
Lake Hughes
Lakewood
Lancaster
Lawndale
Littlerock
Llano
Lomita
Long Beach
Los Angeles
Lynwood
Malibu
Manhattan Beach
Marina Del Rey
Maywood
Monrovia
Montebello
Monterey Park
Montrose
Mount Wilson
Newhall
Norwalk
Pacific Palisades
Palmdale
Palos Verdes Peninsula
Paramount
Pasadena
Pearblossom
Playa Del Rey
Playa Vista
Pomona
Porter Ranch
Rancho Palos Verdes
Redondo Beach
Rosemead
Rowland Heights
San Dimas
San Fernando
San Gabriel
San Marino
San Pedro
Santa Clarita
Santa Monica
Sherman Oaks
Sierra Madre
Signal Hill
South El Monte
South Gate
South Pasadena
Stevenson Ranch
Sun Valley
Sunland
Temple City
Toluca Lake
Topanga
Torrance
Tujunga
Valencia
Valley Village
Valyermo
Venice
Verdugo City
Walnut
West Covina
West Hollywood
Whittier
Wilmington
San Fernando Valley
Burbank
Canoga Park
Chatsworth
Encino
Glendale
Granada Hills
Mission Hills
North Hills
North Hollywood
Northridge
Pacoima
Panorama City
Reseda
Studio City
Sylmar
Tarzana
Universal City
Van Nuys
West Hills
Winnetka
Woodland Hills
Ventura County
Brandeis
Camarillo
Fillmore
Moorpark
Newbury Park
Oak Park
Oak View
Ojai
Oxnard
Piru
Point Mugu
Port Hueneme
Santa Paula
Simi Valley
Somis
Thousand Oaks
Ventura
Westlake Village
Your trusted IT managed service provider of strategic IT infrastructure, security and data loss prevention solutions for small to-midsize businesses. As a premier Cisco-certified MSP, Veeam Gold Cloud Services Provider, and active Trust X Alliance member, we provide outsourced and co-managed IT services to LA and Ventura Counties, and Disaster Recovery (DRaaS) nationally.